Proposing a Cybersecurity Model for Electronic Banking Using a Grounded Theory Approach
Keywords:
Cybersecurity, Electronic Banking, Innovative TechnologiesAbstract
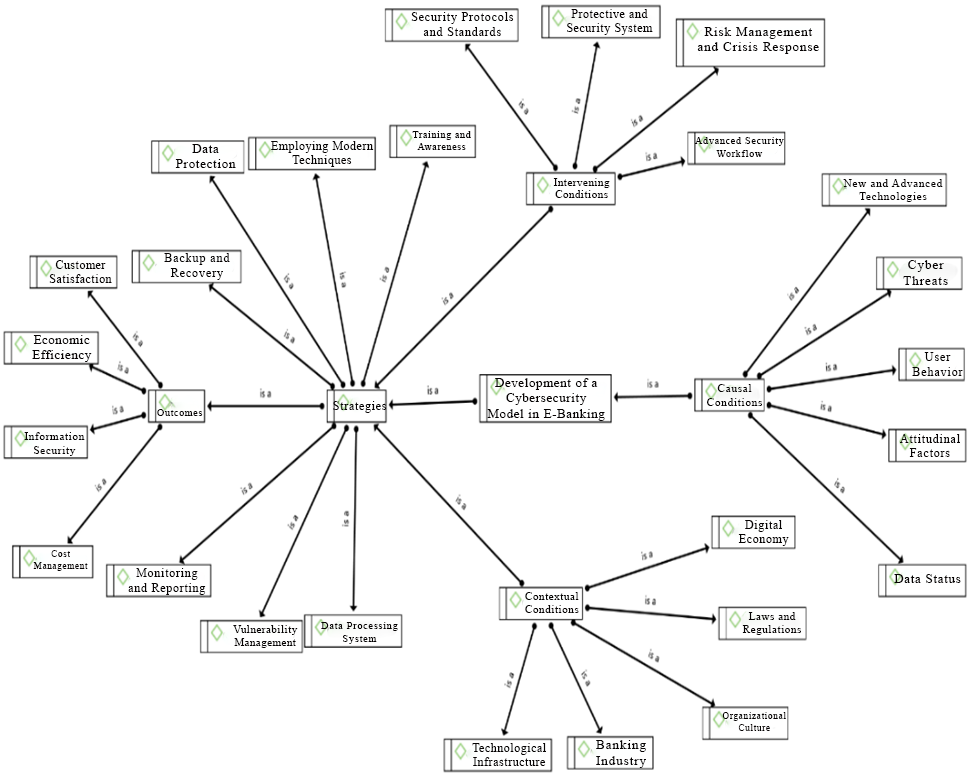
The present study was conducted using a qualitative approach, and the research method was fundamental in terms of its objective. The analysis of this study was carried out using Grounded Theory. The statistical population included experts in electronic banking and cybersecurity from Bank Mellat, cybersecurity specialists from the Ministry of Petroleum, and academic experts. The study was conducted based on the perspectives of 15 experts from these domains. The data collection tool consisted of semi-structured interviews with semi-open-ended questions. Among the identified factors, axial coding was performed, and based on this, a linear relationship was established among the research categories, including core categories, causal conditions, contextual conditions, intervening conditions, strategies, and outcomes, leading to the development of a qualitative research model. The results of this study demonstrated that developing a cybersecurity model for electronic banking is essential, particularly in response to the increasing cybersecurity threats. Since cyber threats against the banking system undermine public trust in governance and pose a threat to national security, utilizing advanced technologies such as blockchain and machine learning, alongside user behavior analysis and organizational culture, can enhance security and increase customer trust in electronic banking services.
References
K. Najaf, C. Schinckus, M. I. Mostafiz, and R. Najaf, "Conceptualising cybersecurity risk of fintech firms and banks sustainability," 2020. [Online]. Available: https://shura.shu.ac.uk/id/eprint/27504.
Y. Kim, Y. J. Park, J. Choi, and J. Yeon, "An empirical study on the adoption of "Fintech" service: Focused on mobile payment services," Advanced Science and Technology Letters, vol. 114, no. 26, pp. 136-140, 2015, doi: 10.14257/astl.2015.114.26.
Y. Creado and V. Ramteke, "Active cyber defence strategies and techniques for banks and financial institutions," Journal of Financial Crime, vol. 27, no. 3, pp. 771-780, 2020, doi: 10.1108/JFC-01-2020-0008.
F. J. Egloff, "Public attribution of cyber intrusions," Journal of Cybersecurity, vol. 6, no. 1, p. tyaa012, 2020, doi: 10.1093/cybsec/tyaa012.
M. Mehenaj Jerin, "Emerging cyber security threats in the banking sector: Loopholes and solutions in the eye of law," International Journal of Law, vol. 10, no. 3, pp. 214-219, 2024.
F. Rajabpour and H. Alizadeh, "Investigating the impact of environmental factors on the adoption of social media among small and medium enterprises during the Covid-19 crisis," in The 6th National Conference and the 3rd International Conference on New Patterns of Business Management in Unstable Conditions, 2024, pp. 1-13. [Online]. Available: https://civilica.com/doc/2098684/.
O. Reis, J. S. Oliha, F. Osasona, and O. C. Obi, "Cybersecurity dynamics in Nigerian banking: trends and strategies review," Computer Science & IT Research Journal, vol. 5, no. 2, pp. 336-364, 2024, doi: 10.51594/csitrj.v5i2.761.
H. M. K. Aldahidhavi, J. Z. S. Abdulreza, M. Sebai, and S. A. Harjan, "An efficient model for financial risks assessment based on artificial neural networks," Journal of Southwest Jiaotong University, vol. 55, no. 3, 2020, doi: 10.35741/issn.0258-2724.55.3.8.
S. Kraus, P. Jones, N. Kailer, A. Weinmann, N. Chaparro-Banegas, and N. Roig-Tierno, "Digital transformation: An overview of the current state of the art of research," Sage Open, vol. 11, no. 3, p. 21582440211047576, 2021, doi: 10.1177/21582440211047576.
H. Alizadeh, K. Alba, and A. Rahdari, "Assessing of the development and sustainability of SMEs based on industry acceptance 4.0," in 1st National Conference on Modern Applied Research in Business and Industrial Development (ARBI2024), 2024, pp. 1-16. [Online]. Available: https://civilica.com/doc/2037846.
H. Alizadeh and M. Foroughi, "A Strategic SWOT Analysis of Leading Electronics Companies based on Artificial Intelligence," International Journal of Business Management and Entrepreneurship (IJBME), vol. 2, no. 2, pp. 1-16, 2023.
D. Sadlakowski and A. Sobieraj, "The development of the FinTech industry in the Visegrad group countries," World Scientific News, vol. 85, pp. 20-28, 2017.
M. S. Kabir and M. N. Alam, "IoT, Big Data and AI Applications in the Law Enforcement and Legal System: A Review," International Research Journal of Engineering and Technology (IRJET), vol. 10, no. 05, pp. 1777-1789, 2023.
C. Van Voorhis, W. Hatcher, T. Kalat, Y. Wang, and E. Hammad, "Towards an Automated Cybersecurity Risk Assessment of Next Generation Emergency Communication Networks-NG911," in 2024 IEEE World Forum on Public Safety Technology (WFPST), 2024, pp. 175-181, doi: 10.1109/WFPST58552.2024.00042.
A. Mehrani, H. Alizadeh, and A. Rasouli, "Evaluation of the Role of Artificial Intelligence Tools in the Development of Financial Services and Marketing," Journal of Technology in Entrepreneurship and Strategic Management, vol. 1, no. 1, pp. 71-82, 2022.
D. P. Widodo, T. Y. R. Syah, and D. A. Negoro, "Digital Channel and Customer Satisfaction on Financial Services," Journal of Multidisciplinary Academic, vol. 4, no. 3, pp. 159-163, 2020. [Online]. Available: https://www.kemalapublisher.com/index.php/JoMA/article/view/461.
A. A. Shaikh, R. Glavee-Geo, H. Karjaluoto, and R. E. Hinson, "Mobile money as a driver of digital financial inclusion," Technological Forecasting and Social Change, vol. 186, p. 122158, 2023, doi: 10.1016/j.techfore.2022.122158.
L. Tristan and P. Thng, "Outsourcing life cycle model for financial services in the fintech era," 2021. [Online]. Available: https://ink.library.smu.edu.sg/sis_research/6116/.
O. Adedoyin Tolulope, O. Chinwe Chinazo, O. Onyeka Chrisanctus, and U. Chinonye Esther, "Cybersecurity risks in online banking: A detailed review and preventive strategies application," World Journal of Advanced Research and Reviews, vol. 21, no. 3, pp. 625-643, 2024, doi: 10.30574/wjarr.2024.21.3.0707.
N. Selvaraj, "The essence of cybersecurity through fintech 3.5 in preventing and detecting financial fraud: a literature review," Electronic Journal of Business and Management, vol. 6, no. 2, pp. 18-29, 2021.
B. Vojdani, "Investigating the Impact of Privacy and Security of Electronic Banking Services on Customer Loyalty with Emphasis on Reliability," in 1st International Conference on Management, Industrial Engineering, Accounting, and Economics in Humanities, 2024. [Online]. Available: https://civilica.com/doc/2025680.
S. A. Mousavi, "Investigating the Impact of Objective Security Dimensions of Electronic Payment Systems on Customers' Perception of Security and Trust (Case Study: Branches of Bank Melli in Kohgiluyeh and Boyer-Ahmad Province)," 2024. [Online]. Available: https://civilica.com/doc/1976050.
A. Parnak, A. Gazari Neishabouri, and B. Seraj, "The Relationship Between Perceived Security and Customer Trust in the NFC-Mobile-Based Electronic Banking System," in 5th International Conference on Interdisciplinary Studies in Management and Engineering, 2022, pp. 674-691.
D. Tahmasebi Aghbolaghi, M. Soltani, M. Shahbazi, and A. Ozaei, "Providing a Strategic Cooperation Framework Between the Private Banking System and FinTechs in Iran," Technology Development Management, vol. 9, no. 1, pp. 41-66, 2021.
S. Goering, A. Beck, N. Dorfman, S. Schwarzwalder, and N. Wohns, "Privacy protections in and across contexts: why we need more than contextual integrity," AJOB Neuroscience, vol. 15, no. 2, pp. 149-151, 2024, doi: 10.1080/21507740.2024.2326932.
R. Evren and S. Milson, "The Cyber Threat Landscape: Understanding and Mitigating Risks," 2024.
S. Anwaar, "Harnessing Large Language Models in Banking: Banking Innovation with Operational and Security Risks," World Journal of Advanced Engineering Technology and Sciences, vol. 13, no. 1, 2024, doi: 10.30574/wjaets.2024.13.1.0426.
N. Afrashteh, A. Mohammadi, A. Ahangari, and A. Asur, "Examining the Challenges and Solutions of Cybersecurity in Today's World," in 2nd International Conference on Management Research, Education, and Training in Education, Tehran, 2024. [Online]. Available: https://civilica.com/doc/2039579.
W. S. Admass, Y. Y. Munaye, and A. A. Diro, "Cyber security: State of the art, challenges and future directions," Cyber Security and Applications, vol. 2, p. 100031, 2024, doi: 10.1016/j.csa.2023.100031.
M. Shekarzehi, B. Hosseinbar, M. Hosseinbar, and A.-K. Arbabanahouk, "The Role of Cybersecurity in IT Education," in 15th International Conference on Management and Humanities Research in Iran, Tehran, Management and Humanities Research Conference in Iran, 2023, vol. 15, 15 ed., pp. 775-780. [Online]. Available: https://civilica.com/doc/2013859.
L. R. Sharma, S. Bidari, D. Bidari, S. Neupane, and R. Sapkota, "Exploring the mixed methods research design: types, purposes, strengths, challenges, and criticisms," Glob Acad J Linguist Lit, vol. 5, 2023.
R. Rohan, D. Pal, J. Hautamäki, S. Funilkul, W. Chutimaskul, and H. Thapliyal, "A systematic literature review of cybersecurity scales assessing information security awareness," Heliyon, vol. 9, no. 3, 2023, doi: 10.1016/j.heliyon.2023.e14234.
I. Negahdar, B. Pourghahramani, and J. Beigi, "Situational Prevention Approaches in Iran's Criminal Policy Towards Cybersecurity Violations in Light of International Documents," Public Policy, vol. 9, no. 2, pp. 97-114, 2023. [Online]. Available: https://civilica.com/doc/1654075.
M. Kumar, "An overview of cyber security in the digital banking sector," East Asian Journal of Multidisciplinary Research, vol. 2, no. 1, pp. 43-52, 2023, doi: 10.55927/eajmr.v2i1.1671.
S. Ahmadi, "Strategies for Developing the Digital Economy in Iran," Economic Security Scientific Monthly, vol. 11, no. 4, pp. 4-16, 2023. [Online]. Available: https://civilica.com/doc/1717234.
P. Zhuang, T. Zamir, and H. Liang, "Blockchain for cybersecurity in smart grid: A comprehensive survey," IEEE Transactions on Industrial Informatics, vol. 17, no. 1, pp. 3-19, 2020, doi: 10.1109/TII.2020.2998479.
A. Mazandarani, M.-T. Kheirabadi, and A. Bazazi, "A Lightweight Location-Aware Authentication Protocol for the Internet of Things," Scientific Journal of Soft Computing and Information Technology, vol. 12, no. 4, pp. 12-22, 2021. [Online]. Available: https://civilica.com/doc/1447733.
M. Golparvar and K. Parsakia, "Building Resilience: Psychological Approaches to Prevent Burnout in Health Professionals," KMAN Counseling & Psychology Nexus, vol. 1, no. 1, pp. 159-166, 01/10 2023, doi: 10.61838/kman.psychnexus.1.1.18.
H. Kaviani and N. Mirsepasi, "Designing an Organizational Capability Model in Cybersecurity," Basij Strategic Studies, vol. 24, no. 92, pp. 121-151, 2021. [Online]. Available: https://civilica.com/doc/1472913.