Providing a Cybersecurity Evaluation Model for Small and Medium Enterprises (SME) (Case Study: Hamoon Nayzeh Pipe Manufacturing Company)
Keywords:
Security, Cybersecurity, Small and Medium Enterprises (SMEs), cybersecurity evaluation, meta-synthesisAbstract
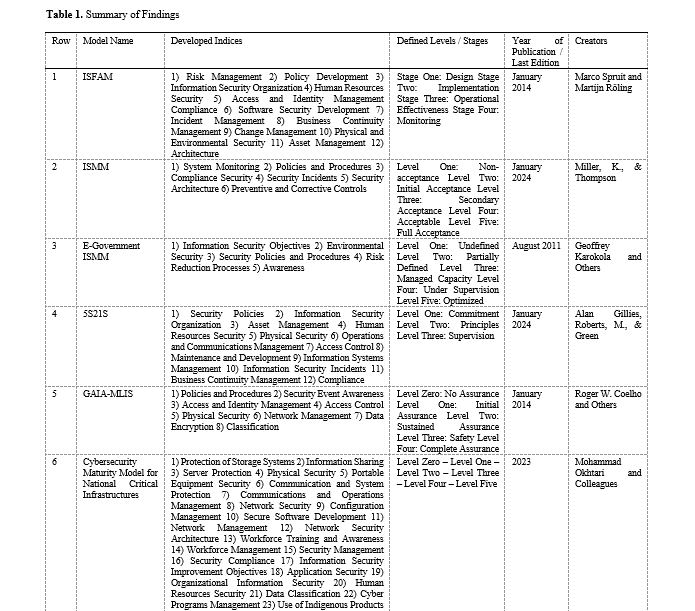
In this study, an effort has been made to design and present a comprehensive and systematic framework for evaluating cybersecurity in small and medium enterprises (SMEs) based on the meta-synthesis approach. This research aims to identify existing models and provide solutions for assessing and improving the cybersecurity status in such companies. The present study is qualitative and utilizes the meta-synthesis approach to analyze and integrate the results of previous research. In this research, all articles published in reputable scientific journals (ISI), books, theses, and internal and external scientific reports related to cybersecurity in SMEs, especially in areas such as cyber threats, data protection, risk management, and security solutions, from 2015 to 2024 were collected and analyzed. After coding and analysis, key factors effective in evaluating the cybersecurity of SMEs were identified. The results from the data analysis indicate that cybersecurity evaluation in SMEs requires a multidimensional approach that, in addition to addressing cyber threats, also considers cultural and organizational aspects. The proposed framework includes various components such as cyber risk assessment, vulnerability identification, evaluating training needs and employee awareness, analyzing cyber threats and attacks, and developing comprehensive security policies. Moreover, the proposed model emphasizes the importance of establishing resilient security infrastructures against threats and utilizing advanced technological tools such as Intrusion Detection Systems (IDS), firewalls, and data encryption.
References
A. T. Chatfield and C. G. Reddick, "A Framework for Internet of Things-Enabled Smart Government: A Case of IoT Cybersecurity Policies and Use Cases in U.S. Federal Government," Government Information Quarterly, vol. 36, no. 2, 2019, doi: 10.1016/j.giq.2018.09.007.
F. Cremer et al., "Cyber Risk and Cybersecurity: A Systematic Review of Data Availability," The Geneva Papers on Risk and Insurance Issues and Practice, 2022, doi: 10.1057/s41288-022-00266-6.
G. Kabanda, C. T. Chipfumbu, and T. Chingoriwo, "A Cybersecurity Model for a Roblox-Based Metaverse Architecture Framework," British Journal of Multidisciplinary and Advanced Studies, vol. 3, no. 2, pp. 105-141, 2022, doi: 10.37745/bjmas.2022.0048.
M. A. Khan and M. Malaika, "Central Bank Risk Management, Fintech, and Cybersecurity," 2021, doi: 10.2139/ssrn.4026279.
N. Kshetri, "Blockchain's Roles in Strengthening Cybersecurity and Protecting Privacy," Telecommunications Policy, vol. 41, no. 10, pp. 1027-1038, 2017, doi: 10.1016/j.telpol.2017.09.003.
S. Kumar and R. R. Mallipeddi, "Impact of cybersecurity on operations and supply chain management: Emerging trends and future research directions," Production and Operations Management, vol. 31, no. 12, pp. 4488-4500, 2022, doi: 10.1111/poms.13859.
P. Radanliev and D. D. Roure, "Advancing the Cybersecurity of the Healthcare System With Self-Optimising and Self-Adaptative Artificial Intelligence (Part 2)," Health and Technology, vol. 12, no. 5, pp. 923-929, 2022, doi: 10.1007/s12553-022-00691-6.
M. Salminen and K. Hossain, "Digitalisation and Human Security Dimensions in Cybersecurity: An Appraisal for the European High North," Polar Record, 2018, doi: 10.1017/s0032247418000268.
K. Smith and G. Dhillon, "Assessing Blockchain Potential for Improving the Cybersecurity of Financial Transactions," Managerial Finance, 2019, doi: 10.1108/mf-06-2019-0314.
M. Swan, "Anticipating the Economic Benefits of Blockchain," (in eng), Technology Innovation Management Review, vol. 7, no. 10, pp. 6-13, 10/2017 2017. [Online]. Available: http://doi.org/10.22215/timreview/1109.
H. Alizadeh and H. Foroughi, "A Strategic SWOT Analysis of Leading Electronics Companies based on Artificial intelligence," International Journal of Business Management and Entrepreneurship, vol. 2, no. 3, pp. 59-74, 2023. [Online]. Available: https://mbajournal.ir/index.php/IJBME/article/view/42.
H. Alizadeh and F. Rajab pour, "Investigating the impact of environmental factors on the adoption of social media among small and medium enterprises during the Covid-19 crisis," in The 6th National Conference and the 3rd International Conference on New Patterns of Business Management in Unstable Conditions, 2024. [Online]. Available: https://civilica.com/doc/2098684/.
G. M. M. Catagua, "Information Security in the Metaverse: A Systematic and Prospective Review," Código Científico Revista De Investigación, vol. 4, no. 2, pp. 781-817, 2023, doi: 10.55813/gaea/ccri/v4/n2/257.
G. Saridakis, V. Benson, J.-N. Ezingeard, and H. Tennakoon, "Individual information security, user behaviour and cyber victimisation: An empirical study of social networking users," Technological Forecasting and Social Change, vol. 102, pp. 320-330, 2016. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0040162515002590.
L. Bahrami, N. Safaie, and H. Hamidi, "Effect of motivation, opportunity and ability on human resources information security management considering the roles of Attitudinal, behavioral and organizational factors," International Journal of Engineering, Transactions C: Aspects, vol. 34, no. 12, pp. 2624-2635, 2021, doi: 10.5829/ije.2021.34.12c.07.
O. Ganji Bidmeshk and S. A. Hosseini Seno, "Proposing and Testing the Model of Aligning the Marketing Information Security Policy with Strategic Information Systems Plan (Case Study: Ferdowsi University of Mashhad)," (in en), New Marketing Research Journal, vol. 5, no. 4, pp. 73-98, 2016. [Online]. Available: https://nmrj.ui.ac.ir/article_17825.html.