An Optimized Feature Selection and Classification Framework for Detecting DDoS Attacks in IoT Networks
Keywords:
DDoS Attack, Internet of Things, Artificial bee colony algorithm, Neighborhood Component Analysis, AdaBoostAbstract
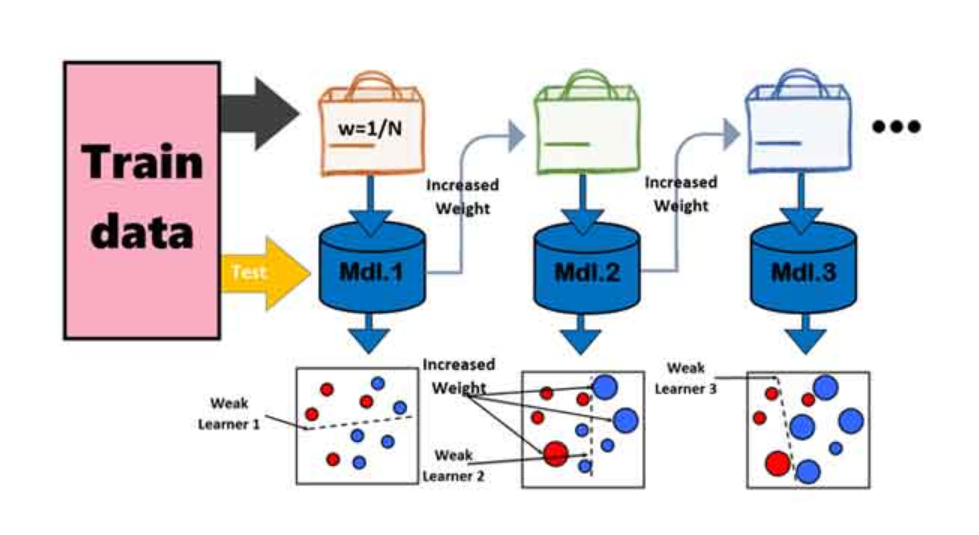
This paper presents the solution of an intrusion detection system to bolster the security of Network infrastructure IoT systems. The proposed method starts with a preprocessing stage of data cleaning, Min-Max normalization, label splitting, conversion of text into numbers, and data partitioning. Important to note, the Artificial Bee Colony Algorithm (ABC) and Neighborhood Component Analysis (NCA) work together in this approach. The initial NCA parameter will be optimized using BCO, whereas the feature selection's effectiveness is evaluated with the Cross Entropy Loss cost function. The final steps include designing and training an ensemble AdaBoost model to the targeted features to maximize accuracy of intrusion detection. Our method has been tested on the NSL-KDD dataset and reports 120 percent training accuracy and 99.74 percent accuracy for test data. With attention to detail, this proposal improves the process of IoT threat detection, unmanned network defense security systems, and poses an efficient method for the advanced dynamic environments, optimizing threading detection, and maximizing military grade precision in modern network security.
References
A. K. Dey, G. P. Gupta, and S. P. Sahu, "Hybrid meta-heuristic based feature selection mechanism for cyber-attack detection in IoT-enabled networks," Procedia Computer Science, vol. 218, pp. 318-327, 2023, doi: 10.1016/j.procs.2023.01.014.
A. G. A. U. S. N. A. Ayad and N. A. Hikal, "A hybrid approach for efficient feature selection in anomaly intrusion detection for IoT networks," The Journal of Supercomputing, vol. 80, no. 19, pp. 26942-26984, 2024, doi: 10.1007/s11227-024-06409-x.
M. A. H. Azmi, C. F. M. Foozy, K. A. M. Sukri, N. A. Abdullah, I. R. A. Hamid, and H. Amnur, "Feature Selection Approach to Detect DDoS Attack Using Machine Learning Algorithms," JOIV: International Journal on Informatics Visualization, vol. 5, no. 4, pp. 395-401, 2021, doi: 10.30630/joiv.5.4.734.
T. Khempetch and P. Wuttidittachotti, "DDoS attack detection using deep learning," IAES International Journal of Artificial Intelligence, vol. 10, no. 2, pp. 382-388, 2021, doi: 10.11591/ijai.v10.i2.pp382-388.
A. Ahmim, F. Maazouzi, M. Ahmim, S. Namane, and I. B. Dhaou, "Distributed denial of service attack detection for the Internet of Things using hybrid deep learning model," IEEE Access, vol. 11, pp. 119862-119875, 2023, doi: 10.1109/ACCESS.2023.3327620ER -.
F. M. Aswad, A. M. S. Ahmed, N. A. M. Alhammadi, B. A. Khalaf, and S. A. Mostafa, "Deep learning in distributed denial-of-service attacks detection method for Internet of Things networks," Journal of Intelligent Systems, vol. 32, no. 1, p. 20220155, 2023, doi: 10.1515/jisys-2022-0155.
M. B. Farukee, M. Z. Shabit, M. R. Haque, and A. S. Sattar, "DDoS attack detection in IoT networks using deep learning models combined with random forest as feature selector," 2021, pp. 118-134, doi: 10.1007/978-981-33-6835-4_8.
M. Roopak, G. Y. Tian, and J. Chambers, "An intrusion detection system against DDoS attacks in IoT networks," 2020, pp. 0562-0567, doi: 10.1109/CCWC47524.2020.9031206.
M. E. Manaa, S. M. Hussain, S. A. Alasadi, and H. A. Al-Khamees, "DDoS attacks detection based on machine learning algorithms in IoT environments," Inteligencia Artificial, vol. 27, no. 74, pp. 152-165, 2024, doi: 10.4114/intartif.vol27iss74pp152-165.
I. Jebril, M. A. U. A. G. M. Premkumar, S. R. Ashokkumar, S. Dhanasekaran, O. I. Khalaf, and S. Algburi, "Deep Learning based DDoS Attack Detection in Internet of Things: An Optimized CNN-BiLSTM Architecture with Transfer Learning and Regularization Techniques," Infocommunications Journal, vol. 16, no. 1, 2024, doi: 10.36244/ICJ.2024.1.1.
J. Shareena, A. Ramdas, and H. Ap, "Intrusion detection system for iot botnet attacks using deep learning," SN Computer Science, vol. 2, no. 3, pp. 1-8, 2021, doi: 10.1007/s42979-021-00516-9.
G. D. L. T. Parra, P. Rad, K. K. R. Choo, and N. Beebe, "Detecting Internet of Things attacks using distributed deep learning," Journal of Network and Computer Applications, vol. 163, p. 102662, 2020, doi: 10.1016/j.jnca.2020.102662.
M. Shurman, R. Khrais, and A. Yateem, "DoS and DDoS attack detection using deep learning and IDS," Int. Arab J. Inf. Technol, vol. 17, no. 4A, pp. 655-661, 2020, doi: 10.34028/iajit/17/4A/10.
A. A. Alahmadi et al., "DDoS attack detection in IoT-based networks using machine learning models: A survey and research directionsJO - Electronics," vol. 12, no. 14, p. 3103, 2023, doi: 10.3390/electronics12143103.
M. Esmaeili, S. H. Goki, B. H. K. Masjidi, M. Sameh, H. Gharagozlou, and A. S. Mohammed, "ML‐DDoSnet: IoT intrusion detection based on denial‐of‐service attacks using machine learning methods and NSL‐KDD," Wireless Communications and Mobile Computing, vol. 2022, no. 1, p. 8481452, 2022, doi: 10.1155/2022/8481452.
A. Gupta, O. Tyagi, V. Uniyal, S. Singhal, and V. Jha, "A Review on Machine Learning Techniques for DDoS Attack Detection in IoT," 2022, pp. 1-6, doi: 10.1109/AIST55798.2022.10064846.
N. Kumar, A. Aleem, and S. Kumar, "Detection of DDoS attack in IoT using machine learning," 2021, pp. 190-199, doi: 10.1007/978-3-030-96040-7_15.
R. E. Schapire, Explaining adaboost. 2013, pp. 37-52.
T. K. An and M. H. Kim, "A new diverse AdaBoost classifier," 2010, vol. 1, pp. 359-363, doi: 10.1109/AICI.2010.82.
W. Hu, W. Hu, and S. Maybank, "Adaboost-based algorithm for network intrusion detection," IEEE Transactions on Systems, Man, and Cybernetics, Part B (Cybernetics), vol. 38, no. 2, pp. 577-583, 2008, doi: 10.1109/TSMCB.2007.914695.
J. C. Bansal, H. Sharma, and S. S. Jadon, "Artificial bee colony algorithm: a survey," International Journal of Advanced Intelligence Paradigms, vol. 5, no. 1-2, pp. 123-159, 2013, doi: 10.1504/IJAIP.2013.054681.
B. Kumar and D. Kumar, "A review on Artificial Bee Colony algorithm," International Journal of Engineering & Technology, vol. 2, no. 3SP - 175, 2013, doi: 10.14419/ijet.v2i3.1030.
D. Karaboga, Artificial bee colony algorithm. 2010, p. 6915.
T. A. Tang, L. Mhamdi, D. McLernon, S. A. R. Zaidi, M. Ghogho, and F. El Moussa, "DeepIDS: Deep learning approach for intrusion detection in software defined networking," Electronics, vol. 9, no. 9, p. 1533, 2020, doi: 10.3390/electronics9091533.
R. Chaganti, W. Suliman, V. Ravi, and A. Dua, "Deep learning approach for SDN-enabled intrusion detection system in IoT networks," Information, vol. 14, no. 1, p. 41, 2023, doi: 10.3390/info14010041.
Downloads
Published
Submitted
Revised
Accepted
Issue
Section
License
Copyright (c) 2025 Haider AL-Husseini , Mohammad Mehdi Hosseini, Murtadha A Alazzawi , Ahmad Yousofi (Author)

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.











